Star programs
الخميس، 19 يوليو 2012
الثلاثاء، 22 نوفمبر 2011
Norton Internet Security+Antivirus-2012 Lifetime License Win-7-Compatible
software
Norton Internet Security+Antivirus-2012 Lifetime License Win-7-Compatible

Norton Internet Security + Antivirus 2012 Lifetime License | 320MB
Norton Internet Security runs quietly in the background to detect and block today's complex threats and to protect your identity when you buy, bank, or browse online. The friendly and efficient product design helps minimize confusing security alerts and system slowdowns that can get in the way of your online experience. Norton Internet Security- provides essential protection from viruses, hackers, spyware, spam and other privacy threats.
A comprehensive set of security tools, Norton Internet Security helps keep you safe online as you surf and email, swap files, download programs, and chat. In addition to protecting against viruses and unwelcome intrusions from the Internet.
NIS also allows you to automatically block annoying banner ads and pop-up windows, set up parental site blocking options for restricting access to specific Web sites, and selectively determine which, if any, Java applets and ActiveX controls should be allowed to download and execute on your computer. Enjoy the Internet with award-winning protection!
Key Technologies:
- Anti Virus
- Anti Rootkit
- Bot Protection
- Norton- Safe Web
- Smart Firewall
- NEW! SONAR- 2 Behavioral Protection
- NEW! Norton System Insight
- NEW! Norton Insight Network AntiSpam
- NEW! Norton Download Insight
- NEW! Norton Threat Insight
- Spyware Protection
- Identity Protection
- Pulse Updates
- Network Monitoring
- Parental Controls
- Vulnerability Protection
- NEW! Professional Strength AntiSpam
- NEW! Norton File Insight
Key Benefits:
- NEW Delivers clear threat and performance explanations-Gives you greater insight into downloaded applications and files by telling you where they came from, if they can be trusted, and how they may impact your PC-s resources and performance.
- NEW Identifies unsafe web sites right in your search results-Warns you of dangerous web sites and suspicious sellers so you can surf and shop online with confidence.
- IMPROVED! Stops online identity theft, viruses, spyware, bots and more-Guards your PC, online activities, and your identity against all types of Internet threats.
- IMPROVED! Stops attacks before they get on your PC-Proactively blocks hackers and prevents dangerous software from downloading to your computer when you surf the web.
- Uses intelligence-driven Norton Insight Network for faster, fewer, shorter scans-Detects and eliminates dangerous software with the shortest scan times of any security product.
A comprehensive set of security tools, Norton Internet Security helps keep you safe online as you surf and email, swap files, download programs, and chat. In addition to protecting against viruses and unwelcome intrusions from the Internet.
NIS also allows you to automatically block annoying banner ads and pop-up windows, set up parental site blocking options for restricting access to specific Web sites, and selectively determine which, if any, Java applets and ActiveX controls should be allowed to download and execute on your computer. Enjoy the Internet with award-winning protection!
Key Technologies:
- Anti Virus
- Anti Rootkit
- Bot Protection
- Norton- Safe Web
- Smart Firewall
- NEW! SONAR- 2 Behavioral Protection
- NEW! Norton System Insight
- NEW! Norton Insight Network AntiSpam
- NEW! Norton Download Insight
- NEW! Norton Threat Insight
- Spyware Protection
- Identity Protection
- Pulse Updates
- Network Monitoring
- Parental Controls
- Vulnerability Protection
- NEW! Professional Strength AntiSpam
- NEW! Norton File Insight
Key Benefits:
- NEW Delivers clear threat and performance explanations-Gives you greater insight into downloaded applications and files by telling you where they came from, if they can be trusted, and how they may impact your PC-s resources and performance.
- NEW Identifies unsafe web sites right in your search results-Warns you of dangerous web sites and suspicious sellers so you can surf and shop online with confidence.
- IMPROVED! Stops online identity theft, viruses, spyware, bots and more-Guards your PC, online activities, and your identity against all types of Internet threats.
- IMPROVED! Stops attacks before they get on your PC-Proactively blocks hackers and prevents dangerous software from downloading to your computer when you surf the web.
- Uses intelligence-driven Norton Insight Network for faster, fewer, shorter scans-Detects and eliminates dangerous software with the shortest scan times of any security product.
Downlaod Link
Filsonic
http://www.filesonic.com/file/3539311805/Norton.IS.AV.2012.19.rar
Wupload
http://www.wupload.com/file/2301880292/Norton.IS.AV.2012.19.rar
DefenseWall Personal Firewall 3.16 + DefenseWall HIPS 3.16 (Eng/Rus)
software
DefenseWall Personal Firewall 3.16 + DefenseWall HIPS 3.16 (Eng/Rus)

DefenseWall Personal Firewall 3.16 + DefenseWall HIPS 3.16 (Eng/Rus) | 18.15 MB
DefenseWall Personal Firewall - the world's first personal firewall, sandbox! For the ordinary user it is very difficult to configure and use the usual "classical" firewalls. The vast majority of panic when he sees a lot of windows with obscure them from security issues, which need something to respond. Most of the answers to such questions are far from correct, allowing malicious code to do its work on the user's computer.
DefenseWall Personal Firewall is totally different from the standard, "classical" schemes of work in software security. You hardly even notice it at work, automatically providing the highest possible level of security immediately after installation.
DefenseWall is based on the concept of "sandbox" that uses untrusted software restriction zone of rights and a bit of virtualization. The new version of the program is integrated bi-directional firewall. This means that malicious applications can not only infect your computer and transmit information via the Internet attackers.
Malware software (including viruses) do not materialize on your hard drive from the expanse of the universe, and come through the quite tangible sources of contamination browsers, USB-flash drives, email, IRC, multimedia clients, ICQ (instant messaging clients), Skype, P2P (eg, through the torrent). These programs all thumbnails are automatically added to the untrusted zone DefenseWall. If any malicious code tries to attack your computer, using untrusted sources for the spread of computer, all attempts to infect your machine or steal confidential information (usernames, passwords) are unsuccessful. A component control connections to the internet will make it impossible to attempt to transfer information from your computer to hackers.
DefenseWall protects you immediately after installation, no training mode does not. For more information, refer to "the technical part," below.
Try DefenseWall Personal Firewall now and you'll be pleasantly surprised by the simplicity of the program ratio and the level of their own security.
Technical section:
In terms of "trusted / untrusted zone ', control of inbound works as follows. It blocks the "listening" ports of trusted processes, since they are potential sources of attacks on the trusted zone sandbox. Only non-trusted processes can work with such ports, unless they, of course, permitted to access the Internet. In the case of incoming attack on the listener port, the attacker gets right into the sandbox, which will not cause substantial harm to the system.
In a corporate setting, DefenseWall automatically opens the 445, 136, 137, 138, and 139 ports. However, untrusted processes can not get access to these ports. This greatly minimizes the possibility of attacks. If you have installed and run the server HTTP / FTP / SMTP / proxy, you must add them to the list of untrusted applications as a potential source of danger from the threat of external attacks on their vulnerabilities.
Some features:
* No learning period (as in the classical solutions).
* The absolute minimum of windows with confirmation in the industry.
* Full compatibility with other solutions in the security field.
* No need to configure anything (configure ports, sockets, ...).
* No need to verify the changed application.
DefenseWall HIPS (Host Intrusion Prevention System) - this is the easiest and simplest way to protect yourself from malicious software, which is not capable of protecting your anti-virus when you're online! Using the technology of next generation proactive protection, DefenseWall help you achieve the maximum level of protection, without requiring you to any special knowledge and constant online updates databases. No signatures, no popup windows, no false positives. It's just a reliable and transparent protection, easy to use and powerful.
DefenseWall HIPS divides all applications into Trusted and nedoverennye.Nedoverennye applications are launched with limited rights to modification of critical system parameters in specially allocated for them in the virtual zone that separates them from trusted applications. In the case of penetration of the untrusted applications malware it will not harm your system and can be closed with just one click! With DefenseWall work on the Internet has never been so easy, safe and easy! Try it and see for yourself!
Why do I need a HIPS if I already have antivirus and firewall?
The firewall monitors only network connections, antivirus protects both from known malicious modules. But the writers of malicious code change them so quickly that antivirus software is not able to detect these modified modules. That's why you need a HIPS-it protects you from malicious applications of all types, known and unknown, without the need for any signatures was.
DefenseWall Personal Firewall - the world's first sandboxing-style personal firewall solution! Average users find it difficult to setup and use your typical firewall and security program. For most average users, program popups and questions are confusing. There is always the chance a user will make the wrong choice and allow malware to cause damage to their system. DefenseWall Personal Firewall is a different kind of security program. You won't even notice it's installed and providing the highest firewall and system protection.
DefenseWall HIPS (Host-based Intrusion Prevention System) is based on a sandboxing approach that uses rights restrictions and partial virtualization. It now comes with an integrated firewall. What this means in simple terms is that malicious files will not have the 'rights' to perform any unwanted changes to your system or be able to make any unwanted connections.
Malware stems from various sources such as internet browsers, usb flash drives, e-mail, multimedia clients, IM, IRC, P2P, and VoIP. All of these programs are automatically marked by DefenseWall HIPS as "untrusted". If malware attempts to install on your system via an "untrusted" program, DefenseWall's inbuilt restrictions (HIPS) will prevent your system from becoming infected. And if malware tries to steal your information such as financial and banking passwords through an "untrusted" program, the Personal Firewall component will stop malware cold from calling home.
And the best part is, DefenseWall protects you right out of the box. For more detailed information, see technical part below.
Try DefenseWall Personal Firewall today, and you will be convinced in its security and simplicity!
Why do I need HIPS if I already have an anti-virus and firewall?
Firewalls control your network activity, antivirus protects you only from known malicious modules. But their writers modify those modules so quickly, that anti-viruses are unable to detect them untill you will be infected with it. That is why you need a HIPS solution-it protects you from all types of malicious software (malware), known and unknown, with no signatures need, proactive way.
Technical section:
In the "trusted / untrusted" terms, Inbound Firewall protection of DefenseWall works as follows: it considers a listening port of a trusted process as a potential source of attack and therefore blocks it. Only "untrusted" processes are allowed to be connected outside. In case of an inbound attack, an attacker is routed to the sandbox. In the corporate environment, DefenseWall automatically opens ports 445, 136, 137, 138, and 139. However, the untrusted processes can't connect to these ports. All of this minimizes potential harm from the malicous code being spread by exploits. If you have a HTTP / FTP / SMTP / proxy server, they should be added to the untrusted applications list as a potential source for vulnerability exploitation and thus a source of infection.
Features:
* No learning modes (as seen with firewall and HIPS programs).
* Mininimal popups.
* Compatible with third-party security software and programs.
* No need to configure ports and sockets.
* No application checksum re-calculations.
Homepage
Download
==========
Filesonic
Mirror
Wupload

DefenseWall Personal Firewall 3.16 + DefenseWall HIPS 3.16 (Eng/Rus) | 18.15 MB
DefenseWall Personal Firewall - the world's first personal firewall, sandbox! For the ordinary user it is very difficult to configure and use the usual "classical" firewalls. The vast majority of panic when he sees a lot of windows with obscure them from security issues, which need something to respond. Most of the answers to such questions are far from correct, allowing malicious code to do its work on the user's computer.
DefenseWall Personal Firewall is totally different from the standard, "classical" schemes of work in software security. You hardly even notice it at work, automatically providing the highest possible level of security immediately after installation.
DefenseWall is based on the concept of "sandbox" that uses untrusted software restriction zone of rights and a bit of virtualization. The new version of the program is integrated bi-directional firewall. This means that malicious applications can not only infect your computer and transmit information via the Internet attackers.
Malware software (including viruses) do not materialize on your hard drive from the expanse of the universe, and come through the quite tangible sources of contamination browsers, USB-flash drives, email, IRC, multimedia clients, ICQ (instant messaging clients), Skype, P2P (eg, through the torrent). These programs all thumbnails are automatically added to the untrusted zone DefenseWall. If any malicious code tries to attack your computer, using untrusted sources for the spread of computer, all attempts to infect your machine or steal confidential information (usernames, passwords) are unsuccessful. A component control connections to the internet will make it impossible to attempt to transfer information from your computer to hackers.
DefenseWall protects you immediately after installation, no training mode does not. For more information, refer to "the technical part," below.
Try DefenseWall Personal Firewall now and you'll be pleasantly surprised by the simplicity of the program ratio and the level of their own security.
Technical section:
In terms of "trusted / untrusted zone ', control of inbound works as follows. It blocks the "listening" ports of trusted processes, since they are potential sources of attacks on the trusted zone sandbox. Only non-trusted processes can work with such ports, unless they, of course, permitted to access the Internet. In the case of incoming attack on the listener port, the attacker gets right into the sandbox, which will not cause substantial harm to the system.
In a corporate setting, DefenseWall automatically opens the 445, 136, 137, 138, and 139 ports. However, untrusted processes can not get access to these ports. This greatly minimizes the possibility of attacks. If you have installed and run the server HTTP / FTP / SMTP / proxy, you must add them to the list of untrusted applications as a potential source of danger from the threat of external attacks on their vulnerabilities.
Some features:
* No learning period (as in the classical solutions).
* The absolute minimum of windows with confirmation in the industry.
* Full compatibility with other solutions in the security field.
* No need to configure anything (configure ports, sockets, ...).
* No need to verify the changed application.
DefenseWall HIPS (Host Intrusion Prevention System) - this is the easiest and simplest way to protect yourself from malicious software, which is not capable of protecting your anti-virus when you're online! Using the technology of next generation proactive protection, DefenseWall help you achieve the maximum level of protection, without requiring you to any special knowledge and constant online updates databases. No signatures, no popup windows, no false positives. It's just a reliable and transparent protection, easy to use and powerful.
DefenseWall HIPS divides all applications into Trusted and nedoverennye.Nedoverennye applications are launched with limited rights to modification of critical system parameters in specially allocated for them in the virtual zone that separates them from trusted applications. In the case of penetration of the untrusted applications malware it will not harm your system and can be closed with just one click! With DefenseWall work on the Internet has never been so easy, safe and easy! Try it and see for yourself!
Why do I need a HIPS if I already have antivirus and firewall?
The firewall monitors only network connections, antivirus protects both from known malicious modules. But the writers of malicious code change them so quickly that antivirus software is not able to detect these modified modules. That's why you need a HIPS-it protects you from malicious applications of all types, known and unknown, without the need for any signatures was.
DefenseWall Personal Firewall - the world's first sandboxing-style personal firewall solution! Average users find it difficult to setup and use your typical firewall and security program. For most average users, program popups and questions are confusing. There is always the chance a user will make the wrong choice and allow malware to cause damage to their system. DefenseWall Personal Firewall is a different kind of security program. You won't even notice it's installed and providing the highest firewall and system protection.
DefenseWall HIPS (Host-based Intrusion Prevention System) is based on a sandboxing approach that uses rights restrictions and partial virtualization. It now comes with an integrated firewall. What this means in simple terms is that malicious files will not have the 'rights' to perform any unwanted changes to your system or be able to make any unwanted connections.
Malware stems from various sources such as internet browsers, usb flash drives, e-mail, multimedia clients, IM, IRC, P2P, and VoIP. All of these programs are automatically marked by DefenseWall HIPS as "untrusted". If malware attempts to install on your system via an "untrusted" program, DefenseWall's inbuilt restrictions (HIPS) will prevent your system from becoming infected. And if malware tries to steal your information such as financial and banking passwords through an "untrusted" program, the Personal Firewall component will stop malware cold from calling home.
And the best part is, DefenseWall protects you right out of the box. For more detailed information, see technical part below.
Try DefenseWall Personal Firewall today, and you will be convinced in its security and simplicity!
Why do I need HIPS if I already have an anti-virus and firewall?
Firewalls control your network activity, antivirus protects you only from known malicious modules. But their writers modify those modules so quickly, that anti-viruses are unable to detect them untill you will be infected with it. That is why you need a HIPS solution-it protects you from all types of malicious software (malware), known and unknown, with no signatures need, proactive way.
Technical section:
In the "trusted / untrusted" terms, Inbound Firewall protection of DefenseWall works as follows: it considers a listening port of a trusted process as a potential source of attack and therefore blocks it. Only "untrusted" processes are allowed to be connected outside. In case of an inbound attack, an attacker is routed to the sandbox. In the corporate environment, DefenseWall automatically opens ports 445, 136, 137, 138, and 139. However, the untrusted processes can't connect to these ports. All of this minimizes potential harm from the malicous code being spread by exploits. If you have a HTTP / FTP / SMTP / proxy server, they should be added to the untrusted applications list as a potential source for vulnerability exploitation and thus a source of infection.
Features:
* No learning modes (as seen with firewall and HIPS programs).
* Mininimal popups.
* Compatible with third-party security software and programs.
* No need to configure ports and sockets.
* No application checksum re-calculations.
Homepage
Download
==========
Filesonic
Mirror
Wupload
Tipard Blu-ray Converter 6.3.10
software
Tipard Blu-ray Converter 6.3.10

Tipard Blu-ray Converter 6.3.10
Tipard Blu-ray Converter is professional Blu-ray Converter to convert Blu-ray disc or Blu-ray m2ts files to DivX, MP4, AVI, 3GP, MPEG, FLV, etc. and HD formats. Moreover, this Blu-ray converter can also rip DVD and convert video files to any others with highest speed and best output quality. Plus, with newly adopted NVIDIA CUDA technology, AMD APP Acceleration and multi-core CPUs supporting technology, the converting speed is 6X faster now.
Convert Blu-ray, DVD and any video
Support automatic deciphering
Put the playlist together for Blu Ray movies
Mighty editing functions
Convert Blu-ray Disc, DVD and video
Powerful Blu-ray Converter, DVD Ripper, and Video Converter
Rip Blu-ray files
Easily rip Blu-ray Disc, DVD or Blu ray files to any other video/audio formats like DivX, MP4, AVI, 3GP, MPEG, FLV and high definition MTS, TS, AVCHD files.
Convert any video files
Support any format of video files (including HD files) and convert any video to other formats for you to enjoy on any players or multimedia devices.
Edit Blu-ray Disc and video
Powerful editing functions to create the perfect output video for you
Crop video
You are allowed to cut off black edges and unwanted playing area. Also you can adjust the video aspect ratio to fit your player’s screen.
Trim and merge
Trim any segment of a Blu-ray movie by setting its start and end time or just dragging the slide bar, and merge several video/DVD pieces together for better watching experience.
Watermark video
Add a text/image watermark to the video. Also you can set its position and transparency.
Preview and Snapshot
The built-in player helps you preview the output video effect. And you and capture your favorite Blu-ray movie pictures and save it as JPEG, GIF or BMP formats. You can also set the saved folder or it will be saved automatically in the defaulted folder.
Set video effect
Adjust the video brightness, saturation and contrast.
Deinterlacing
For the interlaced HD video, check Deinterlacing to convert the interlaced files to the progressive one for you to enjoy successively.
Adjust output settings
Provides you with more choices to make a unique output video
Adjust the specific output parameters
While you convert video or rip DVD, you can set the specific output parameters including Video Encoder, Frame Rate, Video Bitrate, Resolution, Audio Encoder, Sample Rate, Channels, Audio Bitrate. For resolution, you can write in your own parameters.
Audio track and subtitle
Select your preferred audio track and subtitle according to need.
Choose output profile
Tipard Blu-ray Converter provides you with numerous output profiles for you to select.
Load the playlist
This Blu-ray Converter can load the BD playlist to help you figure output the play order.
Fast and easy to use
Provides you with the best user experience
Give you 6X faster converting speed
The newly adopted NVIDIA® CUDA™ technology can totally accelerate your PC GPU, so as to finish your converting task with ultra-high speed and best output quality.
This Blu-ray ripper also supports multi-core CPUs, which can take full advantage of your PC power to accelerate the converting speed.
Automatic decryption
This Blu-ray Converter can automatically decipher your Blu-ray disc.
Easy to use
The intuitive interface can make the operation quite easy, and it is suitable for both beginners and advanced users.
Tipard Blu-ray Converter 6.3.10
WUPLOAD | FILESONIC

Tipard Blu-ray Converter 6.3.10
Tipard Blu-ray Converter is professional Blu-ray Converter to convert Blu-ray disc or Blu-ray m2ts files to DivX, MP4, AVI, 3GP, MPEG, FLV, etc. and HD formats. Moreover, this Blu-ray converter can also rip DVD and convert video files to any others with highest speed and best output quality. Plus, with newly adopted NVIDIA CUDA technology, AMD APP Acceleration and multi-core CPUs supporting technology, the converting speed is 6X faster now.
Convert Blu-ray, DVD and any video
Support automatic deciphering
Put the playlist together for Blu Ray movies
Mighty editing functions
Convert Blu-ray Disc, DVD and video
Powerful Blu-ray Converter, DVD Ripper, and Video Converter
Rip Blu-ray files
Easily rip Blu-ray Disc, DVD or Blu ray files to any other video/audio formats like DivX, MP4, AVI, 3GP, MPEG, FLV and high definition MTS, TS, AVCHD files.
Convert any video files
Support any format of video files (including HD files) and convert any video to other formats for you to enjoy on any players or multimedia devices.
Edit Blu-ray Disc and video
Powerful editing functions to create the perfect output video for you
Crop video
You are allowed to cut off black edges and unwanted playing area. Also you can adjust the video aspect ratio to fit your player’s screen.
Trim and merge
Trim any segment of a Blu-ray movie by setting its start and end time or just dragging the slide bar, and merge several video/DVD pieces together for better watching experience.
Watermark video
Add a text/image watermark to the video. Also you can set its position and transparency.
Preview and Snapshot
The built-in player helps you preview the output video effect. And you and capture your favorite Blu-ray movie pictures and save it as JPEG, GIF or BMP formats. You can also set the saved folder or it will be saved automatically in the defaulted folder.
Set video effect
Adjust the video brightness, saturation and contrast.
Deinterlacing
For the interlaced HD video, check Deinterlacing to convert the interlaced files to the progressive one for you to enjoy successively.
Adjust output settings
Provides you with more choices to make a unique output video
Adjust the specific output parameters
While you convert video or rip DVD, you can set the specific output parameters including Video Encoder, Frame Rate, Video Bitrate, Resolution, Audio Encoder, Sample Rate, Channels, Audio Bitrate. For resolution, you can write in your own parameters.
Audio track and subtitle
Select your preferred audio track and subtitle according to need.
Choose output profile
Tipard Blu-ray Converter provides you with numerous output profiles for you to select.
Load the playlist
This Blu-ray Converter can load the BD playlist to help you figure output the play order.
Fast and easy to use
Provides you with the best user experience
Give you 6X faster converting speed
The newly adopted NVIDIA® CUDA™ technology can totally accelerate your PC GPU, so as to finish your converting task with ultra-high speed and best output quality.
This Blu-ray ripper also supports multi-core CPUs, which can take full advantage of your PC power to accelerate the converting speed.
Automatic decryption
This Blu-ray Converter can automatically decipher your Blu-ray disc.
Easy to use
The intuitive interface can make the operation quite easy, and it is suitable for both beginners and advanced users.
Tipard Blu-ray Converter 6.3.10
WUPLOAD | FILESONIC
VMWare ThinApp 4.7.0 Build 519532
software
VMWare ThinApp 4.7.0 Build 519532
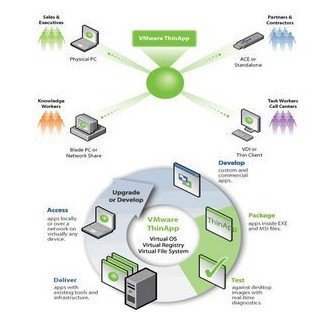
VMWare ThinApp 4.7.0 Build 519532 | 52 MB
Run any version of virtually any application on a single operating system without conflicts. You can even run multiple versions of the same application. Plug VMware ThinApp, formerly known as Thinstall, into your existing management infrastructure and accelerate your software development and desktop deployment. Deliver and deploy applications more efficiently, more securely, and more cost-effectively with agentless application virtualization.
100% Agentless Application Virtualization
• Application isolation. VIsolated applications run in a virtual bubble in restricted user accounts without requiring any host modification. Deploy Office 97, 2003, 2007, and .NET applications on the same OS without conflict as the applications run independent of one another.
• Zero-runtime execution. With no installed agent, no footprint is left on the endpoint device. Applications run directly from the compressed state without first caching data to the hard disk, achieving better performance and security of data.
• 100% User Mode execution. Client runs on locked-down, unmanaged “kiosk” PCs without Admin rights to execute applications, enabling it to be used on managed and unmanaged PC.
• Block-by-block network streaming. Applications virtualized execute once the minimum amount of code required to run the application is available in the desktop’s memory. For example, less than 10% of Microsoft Office needs to be physically streamed to the client in order for it to run. LAN streaming has an average start-up time of just a few seconds.
• Sandbox environments for terminal services. Provide sandboxing for applications running in a terminal services environment so that multiple users can run their own sandboxed application without affecting each other. If one instance of the application tries to make system-wide changes, other users running the same applications are not affected.
• 64-bit operating system support. Enables applications to be virtualized and run on 64-bit systems.
• Execution on thin clients. Tested and certified to run virtualized applications on Windows XP-based thin clients.
• Compatibility with a broad range of applications. Proven deployments on simple-to-complex applications ranging from basic Microsoft Office to custom applications with Java or .NET.
Conflict-free Application Delivery
• Active Directory integration. VMware ThinApp does not require any distribution, streaming, or activation servers or agents. It works with AD, ESD enforcement tools, and open protocols so no additional hardware, software licenses and ongoing maintenance costs for backend infrastructure is required.
• Execution from USB key with portable profiles/user settings. Enable a user to run critical applications from a USB key while maintaining corporate security requirements.
• Integration with 3rd-party application management solutions. Creates .MSI and/or .EXE file that plugs into existing electronic software delivery systems (Inventory, Configuration Management Database, Definitive Software Library, Packagers) without additional integrations required.
• Application Sync. Enables application updates for mobile users as well as third parties on the corporate extranet, ensuring availability of the latest version of the application, reducing patch risks to machines that are taken off the network. Update virtual applications via http/https over the LAN or WAN leveraging existing software delivery systems.
Simplified Application Packaging
• Application Link. Allows packaged applications to dynamically establish dependencies ("links") with other packaged applications. Administers create separate packages of interdependent components such as Java or .NET runtimes and the applications that rely on them. Each component is delivered independently while sharing resources across multiple ThinApp packages.
• Package it once, deliver to many. Execute a packaged application on Windows NT, Windows PE, or XP Embedded without retesting or repackaging the application for each operating system.
• System snapshots. Provides administrators with a rapid three-step process for pre- and post-install system states for packaging simplicity and for supporting applications that require a reboot during the installation process.
• ISV embeddable. Organizations can deliver their custom application throughout their extranet using VMware ThinApp application virtualization technology.
Home Page - www.vmware.com
الخميس، 10 نوفمبر 2011
DAEMON Tools Lite 4.45.1.0236 2012
DAEMON Tools Lite 4.45.1.0236

Daemon Tools - emulator CD / DVD-drives with the support of many security systems. It supports many image formats CD / DVD. The program emulates a conventional disk drives and the type of protection BACKUPcopies (SafeDisc), Securom and Laserlock. A small and handy utility for working with CD images in various formats, including ISO, CCD (CloneCD), BWT (Blindwrite), NRG (Nero), and others. When you start the game using the image of the disk can simulate the conditions to circumvent the many schemes of copy protection. DAEMON Tools can be used as an excellent virtual CD (DVD)-ROM.
The program works through the system tray menu with which you have access to all commands. You can select the number of added virtual drives, mount images for each of them. To identify each drive, you can choose any letter English alphabet, which is available. Also, for each virtual device can be set to your region code. It should be noted that the connection and disconnection of virtual drives occurs almost instantaneously and without having to reboot. Features can be expanded with additional modules, which in large quantities are produced by third parties.
Features:
Create a *. iso and *. mds images
Virtualize up to 4 drives
Work with images formats: *. iso, *. nrg, *. b5t, *. b6t, *. bwt, *. ccd, *. cdi, *. cue, *. isz
Compress and password-protect images
Use a new gadget to the Sidebar in Windows 7, Vista
In this version:
New Features
Support for APE images;
Added a new type of virtual drive emulation for the base - DT;
Improved portable unit;
SPTD 1.78.
Bug Fixes
Incompatibility between DAEMON Tools and Power2Go, PowerDVD;
Ignoring the blocked applications in the removal process.
download
hotfile

DAEMON Tools Lite 4.45.1.0236 | 14 Mb
Daemon Tools - emulator CD / DVD-drives with the support of many security systems. It supports many image formats CD / DVD. The program emulates a conventional disk drives and the type of protection BACKUPcopies (SafeDisc), Securom and Laserlock. A small and handy utility for working with CD images in various formats, including ISO, CCD (CloneCD), BWT (Blindwrite), NRG (Nero), and others. When you start the game using the image of the disk can simulate the conditions to circumvent the many schemes of copy protection. DAEMON Tools can be used as an excellent virtual CD (DVD)-ROM.
The program works through the system tray menu with which you have access to all commands. You can select the number of added virtual drives, mount images for each of them. To identify each drive, you can choose any letter English alphabet, which is available. Also, for each virtual device can be set to your region code. It should be noted that the connection and disconnection of virtual drives occurs almost instantaneously and without having to reboot. Features can be expanded with additional modules, which in large quantities are produced by third parties.
Features:
Create a *. iso and *. mds images
Virtualize up to 4 drives
Work with images formats: *. iso, *. nrg, *. b5t, *. b6t, *. bwt, *. ccd, *. cdi, *. cue, *. isz
Compress and password-protect images
Use a new gadget to the Sidebar in Windows 7, Vista
In this version:
New Features
Support for APE images;
Added a new type of virtual drive emulation for the base - DT;
Improved portable unit;
SPTD 1.78.
Bug Fixes
Incompatibility between DAEMON Tools and Power2Go, PowerDVD;
Ignoring the blocked applications in the removal process.
download
hotfile
الاشتراك في:
الرسائل (Atom)